New issuing CAs for QC eSeal certificates from 23 August, 2021
Introduction
As of Q3 2021, Buypass is making changes to Qualified Certificates for electronic seals (QC eSeal).
These changes are related to national transition to new certificate profiles (see Endringer i Buypass personsertifikater og virksomhetssertifkater - Norwegian only) and leads to better harmonization of certificates with European standards. In addition, Buypass uses new CAs for the issuance of these certificates ('Generation 2 (G2)') and makes changes to increase the security by using stronger cryptography.
Changes to certificate profiles
For qualified certificates for electronic seals, there are a few changes only since these certificates have already been adapted to European standards.
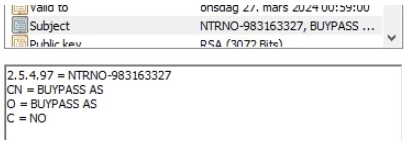
The most important change is that the organization number is now prefixed with a Semantic Identifier (here NTRNO:) in the OrganizationIdentitfier attribute - which in the example below means that the identifier is defined in a 'National Trade Register (NTR)' in Norway (NO):
For more information about the certificate profiles, see Buypass Class 3 certificate profiles.
New G2 CAs
Buypass has established a new set of logical CAs (Generation 2 - G2) that are used to issue personal certificates and enterprise certificates (including QC eSeals).
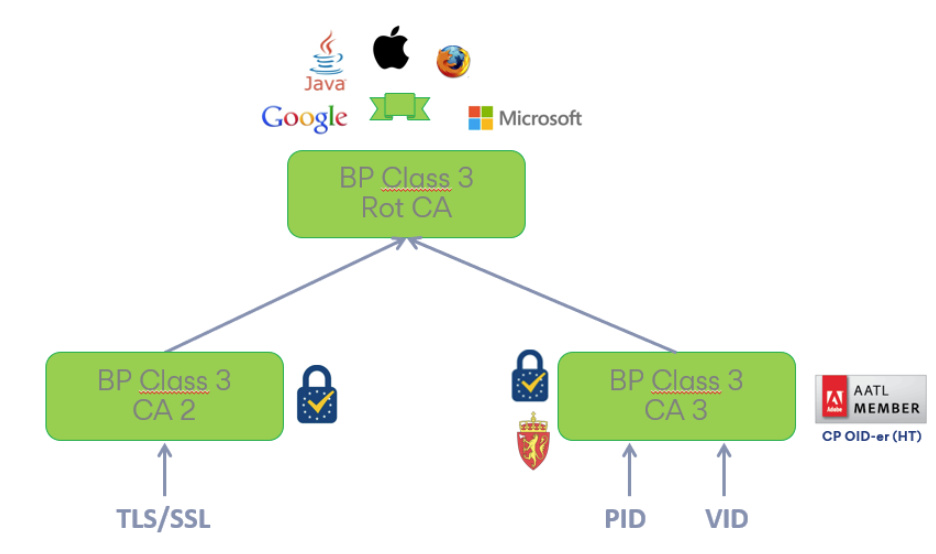
This is how the CA hierarchy looks for what we call Generation 1 CAs:
Here, QC eSeals are issued under Buypass Class 3 CA 3 which chain back to Buypass Class 3 Rot CA. This is a Root CA that is also recognized by browsers and other certificate programs, which puts unnecessary restrictions on the contents of these certificates.
Buypass Class 3 CA 2 is used to issue TLS / SSL certificates, including QWACs (Qualified Website Authentication Certificates) in accordance with the eIDAS Regulation. Both of the two issuing CAs are marked with the eIDAS trust mark since they are both registered on the EU trust list for the issuance of qualified certificates.
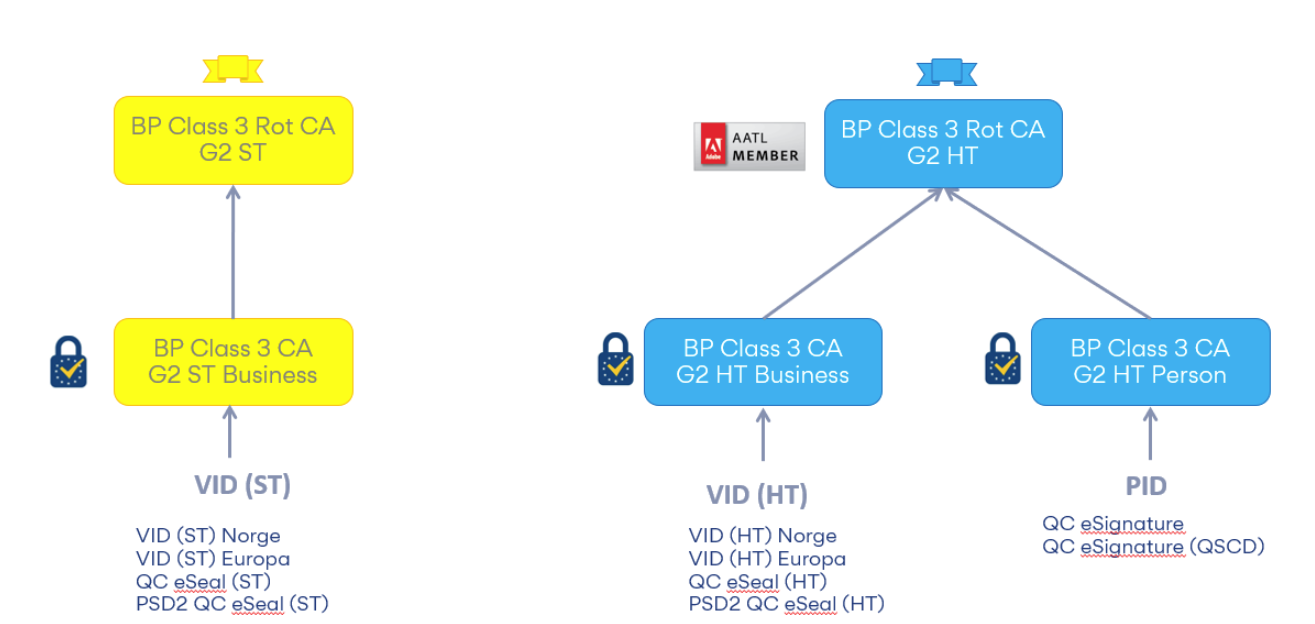
In the new G2 CA structure, the CA hierarchy looks like this:
Here we distinguish between certificates issued on keys that are secured in hardware devices such as smart cards and HSMs (in so-called HardTokens - HT) and certificates issued on keys that are secured in software (SoftTokens - ST). Adobe requires that keys are secured in hardware devices and therefore we have established a separate CA hierarchy where all certificates are recognized by Adobe.
QC eSeals are issued under either Buypass Class 3 CA G2 ST Business or Buypass Class 3 G2 HT Business depending on how the key is secured.
Here, too, all three issuing CAs are marked with the eIDAS trust mark since all three can issue qualified certificates (for electronic seals in the case of the "Business" CAs and electronic signatures in the case of the "Person" CA) .
Buypass Class 3 Root CA G2 HT is included in Adobe's AATL program, otherwise none of these are included in any other certificate programs. This gives greater flexibility and independence for our personal certificates and enterprise certificates and is also in accordance with the current recommendation when it comes to limiting different types of certificates that can be chained back to one and the same root.
Root CA certificates and issuing CA certificates may be downloaded from Buypass Root Certificates. Root CA certificates and issuing CA certificates for test may be downloaded from Root certificates, test.
Stronger cryptography
Current recommendations for the use of cryptographic algorithms, especially for signing, indicate that by 2025 one should switch to stronger cryptography than 2048 bit RSA. With 3 years validity for our qualified certificates, we want to switch to longer RSA keys.
We will also introduce support for elliptic curve cryptography (ECC) and will support curves in the NIST family, especially NIST P-256 from the beginning. This will then make it possible to sign messages with ECDSA using ECC keys. The use of ECC keys significantly reduces the key length while maintaining good security. A 256-bit ECC key will be as (cryptographically) strong as a 3072-bit RSA key.
For more information about cryptographic algorithms we plan to support in the future, see Stronger cryptography (Norwegian only).