Direct Access 2012R2 integration - RADIUS
Requirements
- Direct Access configured and working.
- Buypass Code Service Connector installed according to the installation guide.
- Service account in Active Directory for LDAP queries.
- Access to internal Certificate Authority to configure necessary templates.
- RADIUS port UDP 1812 open between Direct Access server and Buypass Code Service Connector.
- LDAP port TCP 389 open between Buypass Code Service Connector and LDAP server.
- HTTPS port TCP 443 open from Buypass Code Service Connector to the internt.
Integration
Log on to Buypass Code Manager.
https://www.buypass.no/bpcode/merchants/YOURMERCHANTID/logon
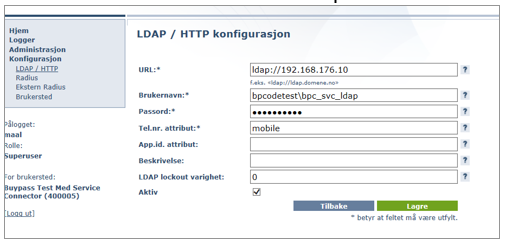
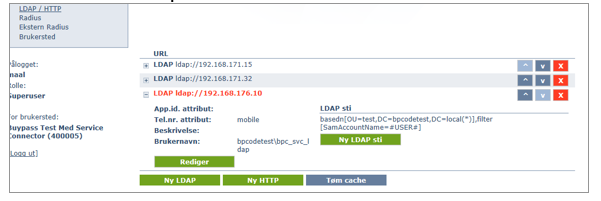
Configure LDAP settings.
- Add new LDAP configuration.
- Add LDAP server IP or FQDN.
- Add service account with read access to LDAP catalog/Active Directory.
- Add name of attribute for mobile phone – AD attribute name is “mobile”.
- Add a new LDAP path.
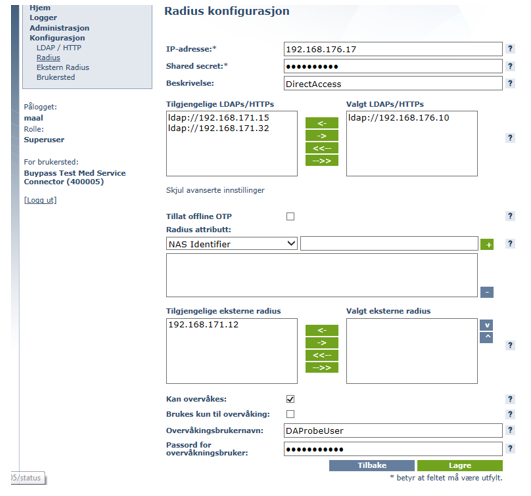
Configure Direct Access as a RADIUS client.
- New RADIUS configuration.
- Add IP address of the Direct Access server.
- Add Shared secret.
- Enter Description.
- Choose LDAP to be used.
- Click on Advanced, choose Can be monitored and configure DAProbeUser and DAProbePass.
- Save.
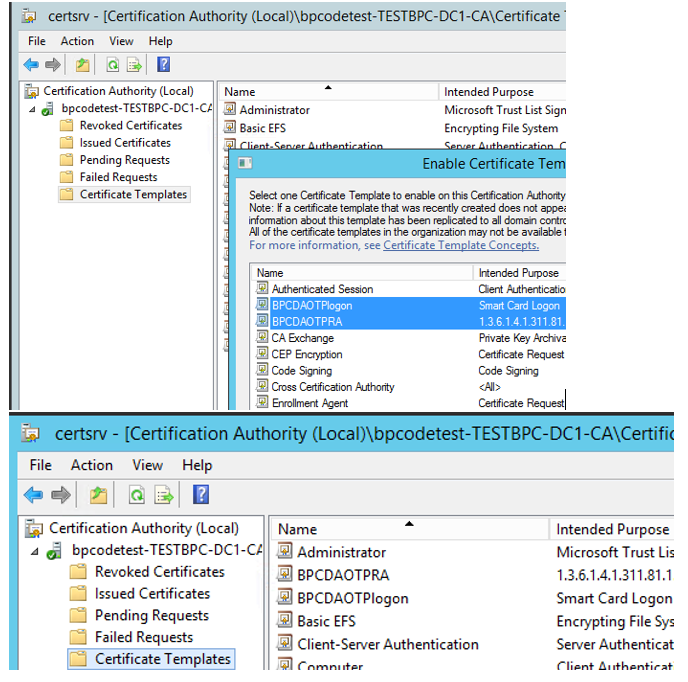
Configure certificate templates.
Configure OTP signing certificate template (registration authority certificate).
- Start Certificate Template console - Start→ certtempl.msc.
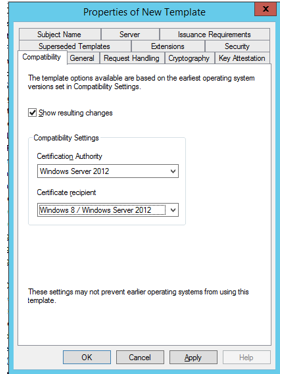
- Duplicate Computer template.
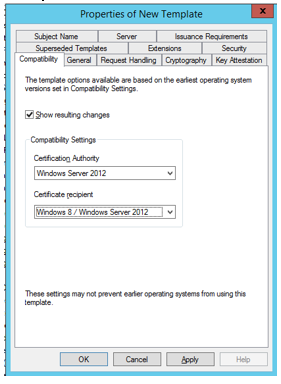
- Compatibility - Under Certification Authority, choose Windows server 2012 or newer and under Certificate recipients Windows 8 / Windows Server 2012 or newer.
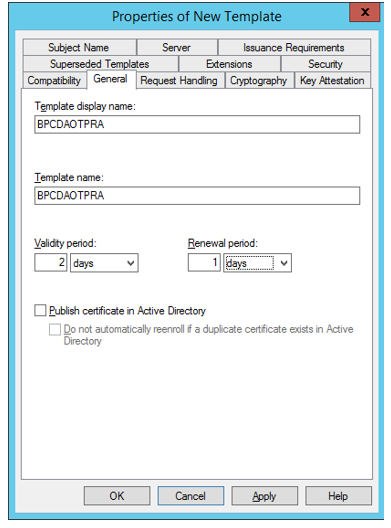
- General - In Template display name, type BPCDAOTPRA, set validity period to 2 days and renewal period to 1 day.
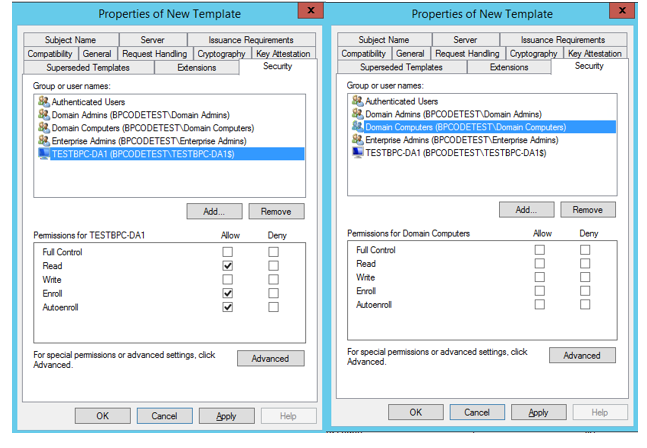
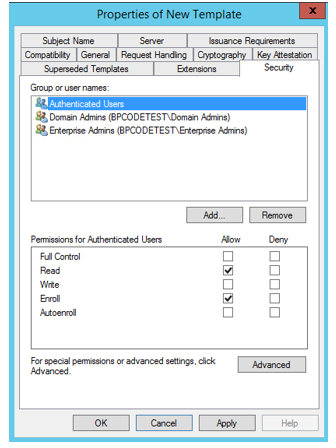
- Security - configure the following settings.
- Direct access server object: Allow READ, ENROLL and AUTO ENROLL.
- Authenticated users: allow READ.
- Domain admins: Allow FULL CONTROL.
- Enterprise admins: Allow FULL CONTROL.
- Domain computers: remove ENROLL from Allow.
- Allow.
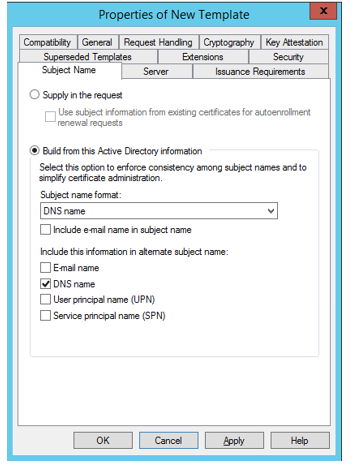
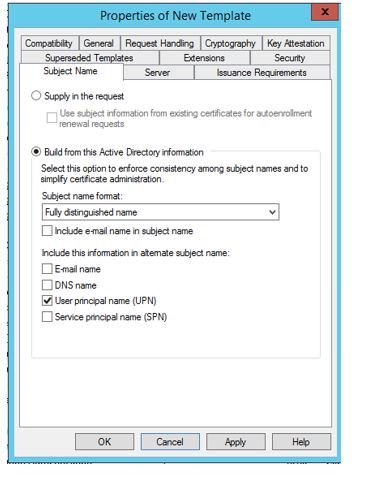
- Subject name - Build from AD. Subject name format, choose DNS name. Check for DNS name box. Apply.
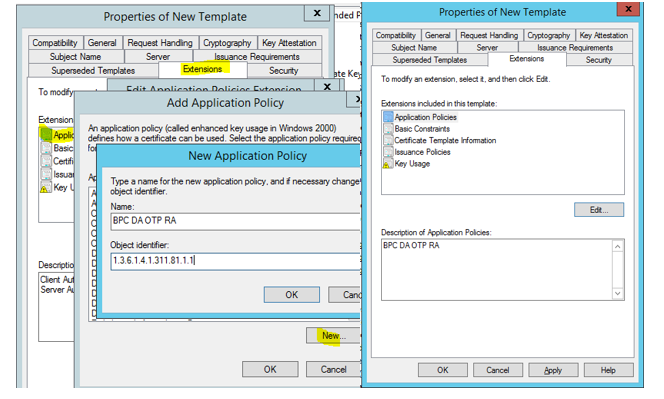
- Extension - Edit Application policy, remove all from the list. Add new - Name BPC DA OTP RA. In Object identifier field, type 1.3.6.1.4.1.311.81.1.1
Configure OTP logon certificate template (OTP authentication certificate)
- Duplicate Smartcard logon template.
- Compatibility - Under Certification Authority, choose Windows Server 2012 or newer. Under Certificate recipients, Choose Windows 8 / Windows Server 2012 or newer.
- General - Type BPCDAOTPlogon in Template Display name. Set validity period to 1 hours and renewal period to 0 hours.
- Security - Configure the following settings:
- Authenticated users: Allow READ and ENROLL.
- Domain admins: Allow FULL CONTROL.
- Enterprise admins: Allow FULL CONTROL.
- Apply
- Subject name - Build from Active directory. Set Subject name format to Fully distinguished name. Check box User Principal Name (UPN).
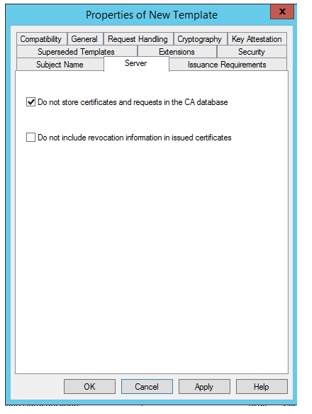
- Server - Choose "Do not store certificates and requests in the CA database". Remove mark from "Do not include revocation information in issued certificate".
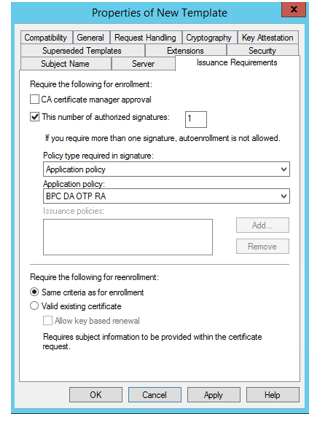
- Issuance requirements - Set "This number of authorized signatures" to 1. Under Policy type required in the signature, choose Application policy. In Application policy, choose BPC DA OTP RA. Click Apply.
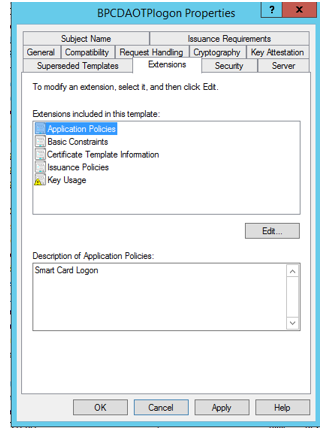
- Extensions - Edit Application policies and remove Client Authentication. Click Apply.
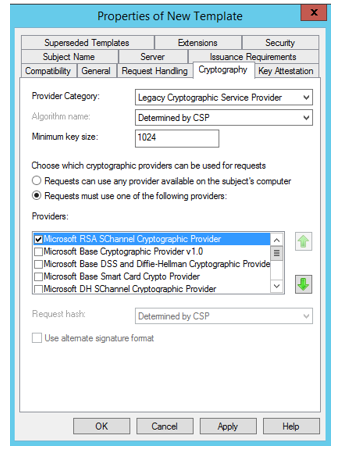
- Cryptography - Minimum Key Size 1024, Request must use one of the following providers: Microsoft RSA SChannel Cryptographic provider. Click OK.
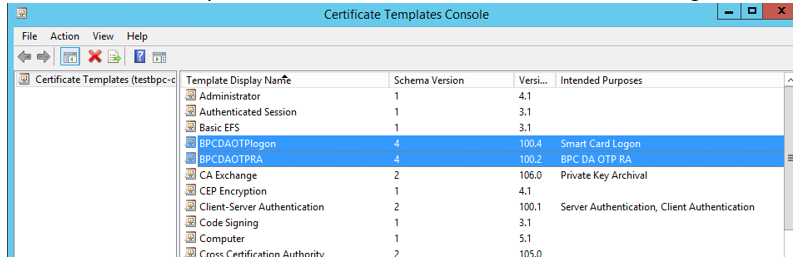
- Check that the new templates has BPC DA OTP RA and Smart Card Logon under Intended Purposes.
- Publish new Templates.
Configure Direct Access with OTP
- Start Remote Access Management. Click Edit in Configuration Wizard, Step 2.
- Click Next to get to Authentication.
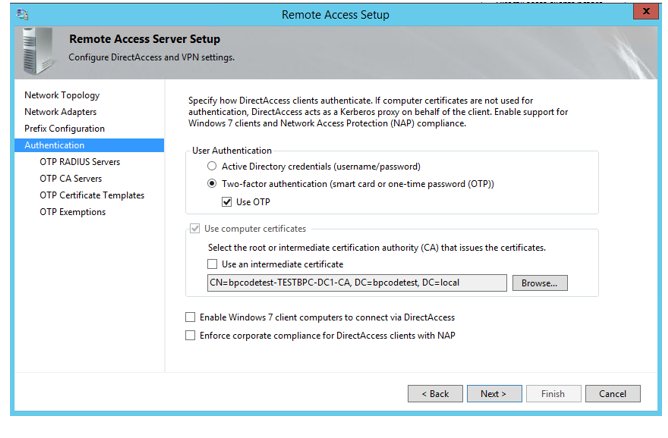
- Choose Two-factor authenticatin and check OTP. "Use computer certificate" should be marked and proper issuing CA should be filled in. Choose if you want to enable Windows 7 computers or not. Click Next.
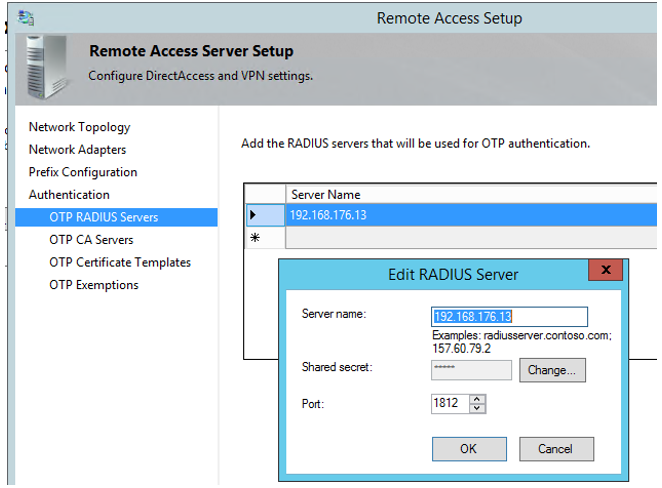
- In Add RADIUS, double-click the first line and add IP address of Buypass Code Service Connector. Click Change and add Shared secret (the same as configured in Buypass Code Manager). Port 1812. Click OK and Next.
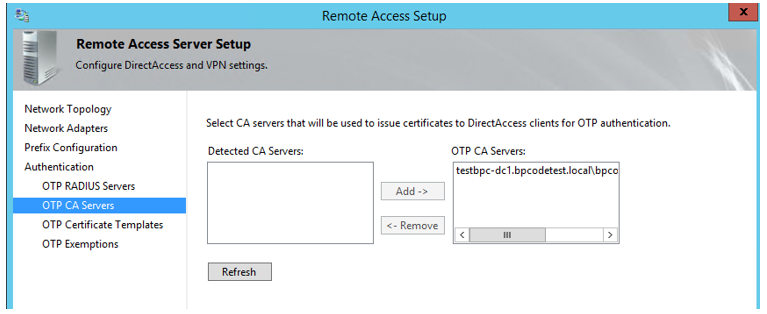
- Add CA Server.
- Choose BPCDAOTPLogon for OTP authentication and BPCDAOTPRA for enrollment request. Click Next.
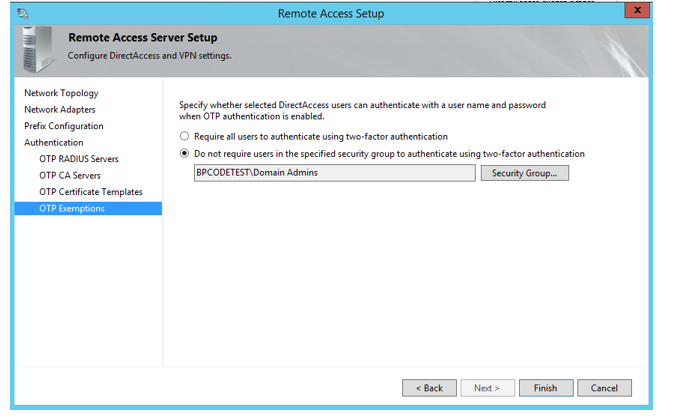
- Choose if you want to exclude an AD group from two factor authentication.
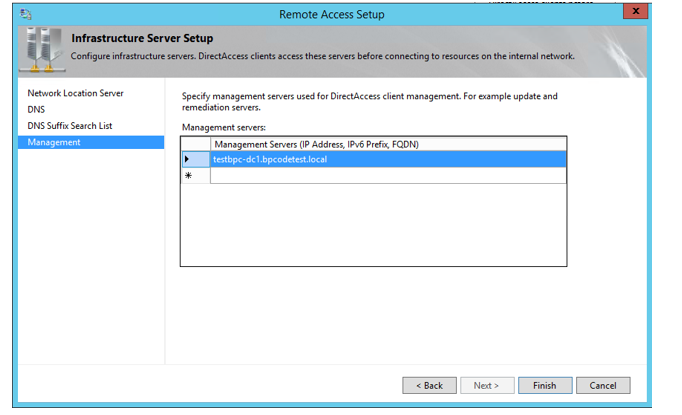
- Under Step 3 of the Configuration wizard, add CA server in the management section.
- Use Powershell to configure Direct Access with OTP:
- Set-DAServer -UserAuthentication TwoFactor
- Enable-DAOtpAuthentication -CertificateTemplateName "BPCDAOTPLogon" -CAServer "testbpc-dc1.bpcodetest.local\bpcodetest-TESTBPC-DC1-CA" -RadiusServer 192.168.176.13 -SharedSecret Abcd123$ -SigningCertificateTemplateName "BPCDATPRA" –Verbose
Test from the client
Logon to Direct Access enabled PC outside of the corporate network (homeoffice, LTE etc.).
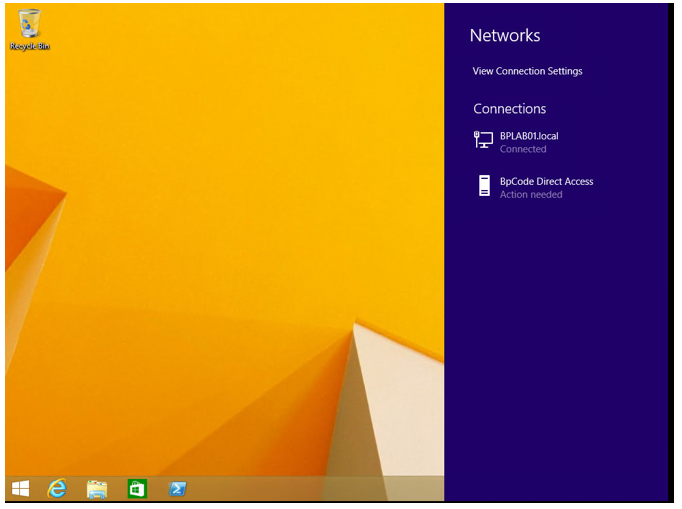
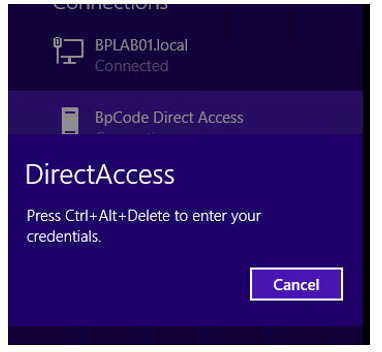
Click on the Network icon, click on Direct Access (Action Needed).
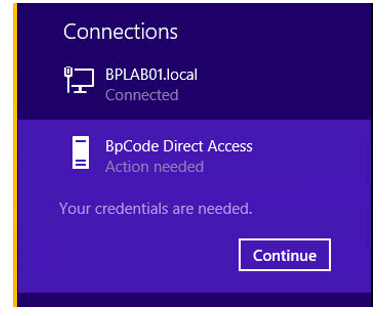
Click Continue.
Press CTRL+ALT+DEL.
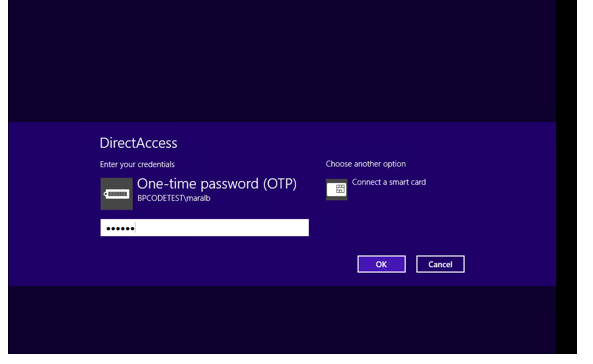
Choose OTP and type code from the Buypass Code App. Click OK.
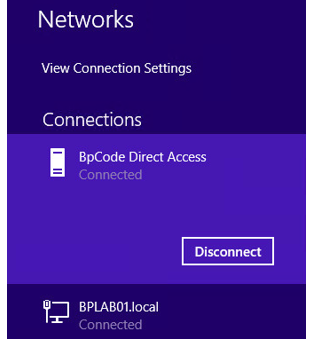
The user is authenticated and can access corporate resources.
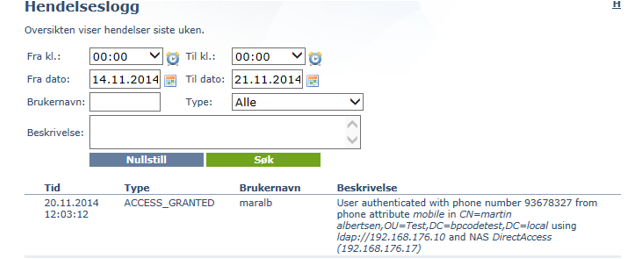
The logon entry is logged in Buypass Code Manager.
Microsoft reference: http://technet.microsoft.com/en-us/library/hh831379.aspx - Deploy remote Access with OTP Authentication