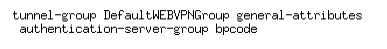Cisco ASA integration - RADIUS
Requirements
- Buypass Code Service Connector is installed and can communicate with LDAP on TCP port 389.
- Service account for LDAP queries is created.
Integration
Log on to Buypass Code Manager for your merchant site.
https://www.buypass.no/bpcode/merchants/YOURMERCHANTCODE/logon
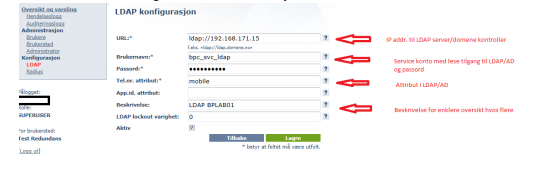
Define the LDAP server and path under the menu Configuration → LDAP
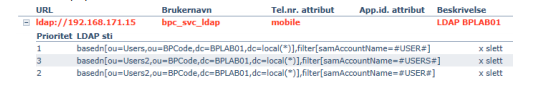
LDAP path(s)
It is possible to define multiple LDAP paths. To do recursive queries add (*) behind the last DC= (DC=local(*)).
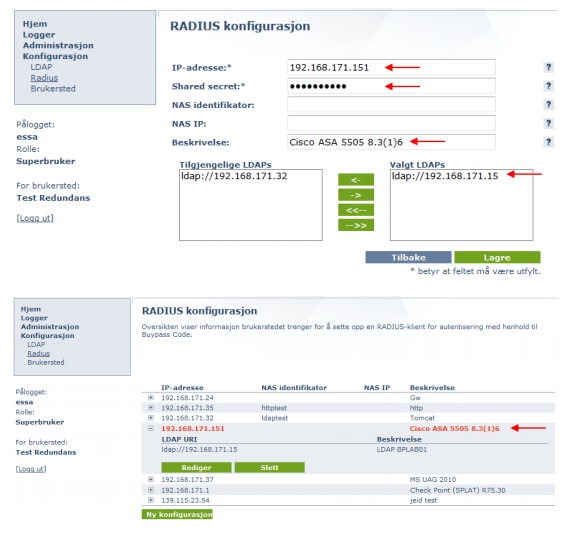
Define the RADIUS client (Confguration → Radius → New Configuration).
Enter the internal IP of the Cisco ASA, shared secret and give a description.
Choose the LDAP(s) to be used and press save.
Log on to the Cisco ASA with Cisco ASDM.
Create a new AAA Server Group under the menu "Configuration - Remote Access VPN".
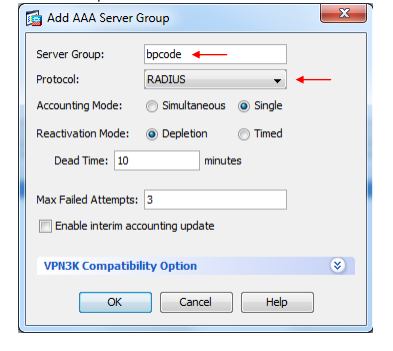
Press Add on the right side of the "AAA Server Groups" page.
Give the group a name, e.g. 'bpcode'.
Choose the protocol RADIUS.
Let the rest of the parameters remain.
Press OK.
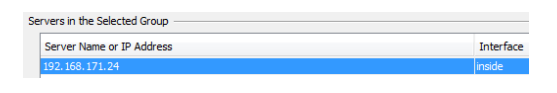
Add a new server(add on the right side) in the newly created group(in the field "Servers in the Selected Group").
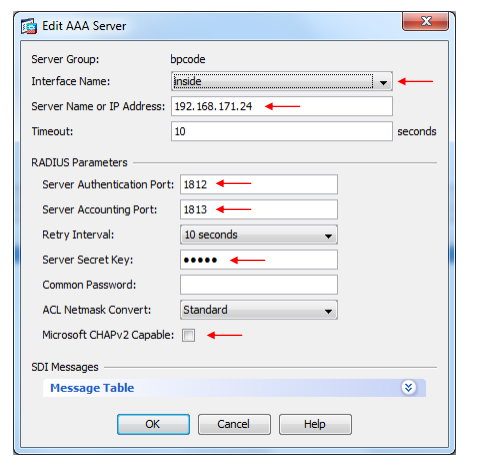
Choose interface "inside".
Enter the IP to the Buypass Code RADIUS Service Connector.
Change "Server Authentication Port" to 1812.
Change "Server Accounting Port" to 1813.
Enter "Server Shared Secret".
Remove the marker for "Microsoft CHAPv2 Capable".
Let the rest of the settings remain.
Press Apply in the bottom of the configuration window.
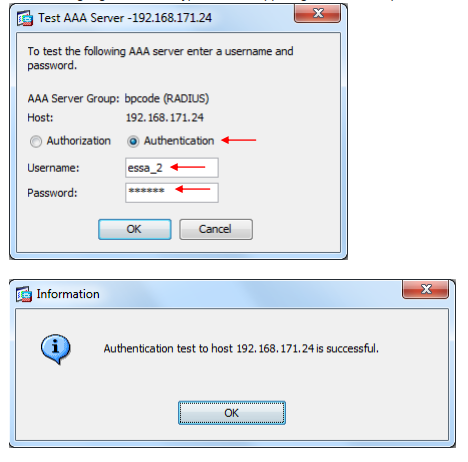
From the same windows you can now test the configuration(Press the button Test on the right side).
Choose Authentication.
Enter the username(the user must exist in LDAP/AD).
Enter the OTP(One Time Password) from the Buypass Code App and press OK.
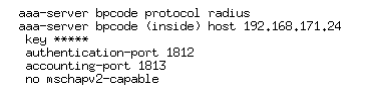
The same configuration can be done through CLI and will then look like:
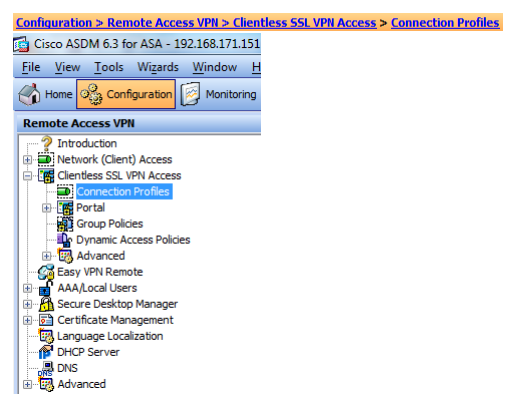
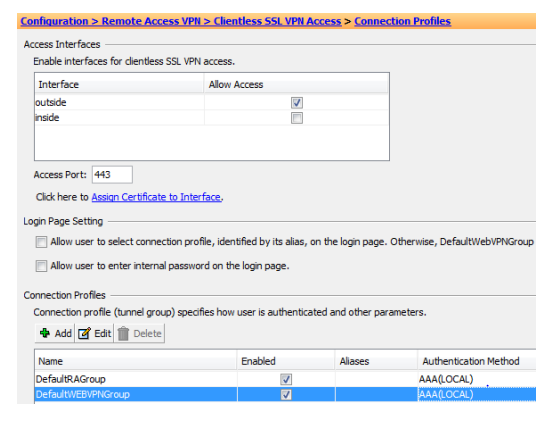
Configure "Clientless SSL VPN Access" to use BP Code (RADIUS).
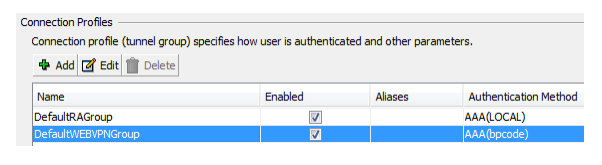
In this case the standard profile is used(DefaultWEBVPNGroup)
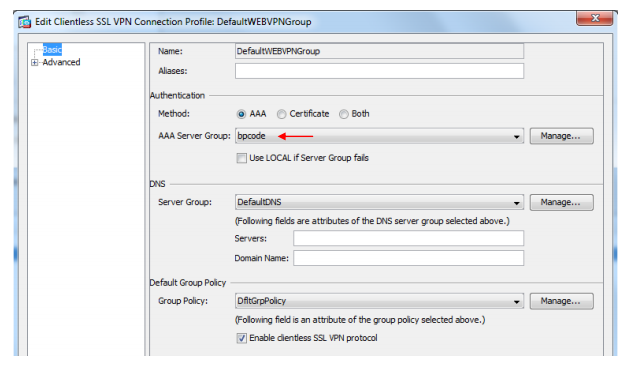
Doubletclick the "DefaultWEBVPNGroup"
Choose "Authentication Method" AAA and then AAA Server Group from P.6.
Remove any marker from "Use LOCAL if Server Group fails".
Press OK.
Press Apply at the bottom of the window.
The same configuration can be done from CLI and will look like:
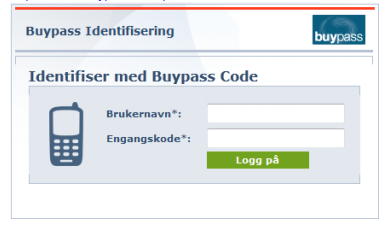
To log on to the Clientless SSL VPN Access (browser based VPN access)
Enter the username (user must exist in LDAP/AD).
Enter the One Time Password from the Buypass Code App and press Login.